Payment in E-Commerce.
Payment in E-Commerce
In any commercial transaction payment is an integral part for goods supplied. Four types of payments may be made in e-commerce they are
•Credit card payments
•Electronic cheque payments
•Micro or small payments for internet based services such as music download.
•Electronic-cash payments
Each of these requires a different system of payment.
Review Of Manual Credit Card Payment
Four parties are invoked in credit card payments. They are:
• Customer having a credit card
• Merchant accepting credit cards (such as VISA, MASTER CARD etc)
• Bank which issues credit cards to customers and collects payments from customers
•Acquirer which is financial institution that establishes an account with a merchant, validates credit card information sent electronically by merchant and authorises sale based on customer’s credit status. Acquirer accepts credit cards of several card companies and guarantees payment to merchants. Acquirer gets reimbursed by bank issuing credit card.
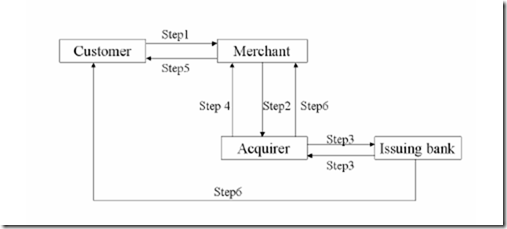
Sequence Of Transactions In Manual Credit Card Payment
Step 1: Customer presents credit card after purchase. Merchant swipes it on his special phone and enters amount
Step 2: Data from merchant’s terminal goes to acquirer via a private telephone line
Step 3: Acquirer checks with the issuing bank validity of card and credit- available
Step 4: Acquirer authorizes sale if all OK and sends approval slip which is printed at merchant’s terminal.
Step 5: Merchant takes customer’s signature on the slip-verifies it with the signature on card and delivers the goods.
Step 6: The acquirer pays the money to merchant and collects it from the appropriate issuing bank. The bank sends monthly statement to customer and collects outstanding amount.
Block Diagram Of Steps In Credit Card Transaction
Credit Card In E-commerce
Main Problems
1. Main Problem is: if a merchant had only a web presence, a Customer needs to be reassured that the merchant is genuine.
2. Customers Signature cannot be physically verified. Customer needs electronic signature.
3. Secrecy of credit card number has to be ensured.
4.Dispute settlement mechanism must be worked out.
Secure Electronic Transaction Protocol
To use SET protocol it is assumed that
1. Each party involved in e-commerce transaction has a public and private key.A public key encryption is used.
2. All parties have their public keys certified.
3. A standard hashing algorithm is used to create message digest for signature verification.
Main Features
•Customers credit card number is not revealed to a merchant. It is revealed only to the acquirer who authorises payment.
•Purchase invoice details are not revealed to the acquirer.Only the credit card number and total amount are revealed to him
•Purchase invoice + credit card number is digitally signed by the customer.In case of a dispute an arbitrator can use this to settle the dispute.
(Computer protocol runs to 262 pages and may be found in www.ibm.com/redbook/SG244978)
DUAL SIGNATURE SCHEME
Dual signature scheme is an innovation in SET protocol
Steps followed in the protocol are:
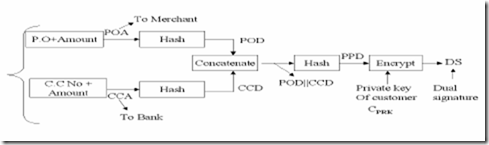
1. Customer purchase information has 3 parts
(i) Purchase Order (PO)
(ii) Credit Card Number (CCN)
(iii) Amount to be paid
2. Merchant should know (PO + Amount)=POA
3. Acquirer should know (CCN+Amount)=CCA
4. Hash POA using standard Hash algorithm such as RSA’s MD5. Call it POD.
5. Hash CCA using MD5. Call it CCD
6. Concatenate POD and CCD. Call it (POD||CCD)
7. Hash (POD||CCD) giving PPD
8. PPD is encrypted using Private key of customer. This is customer’s digitally signed purchase order
DS = Encrypt (PPD) with CPRK
CPRK is Private key of customer. This is sent to merchant by customer. DS is called Dual Signature as a private key is used to sign two separate digests concatenated together.
9. POA separately encrypted by customer using merchant’s public key and sent to merchant
10. Merchant decrypts it using his private key. He thus gets Purchase order +Amount. He can hash it and get POD
11. CCD and DS also sent to merchant. From CCD merchant cannot find CCN.
12. Merchant can decrypt DS using customer’s public key and get PPD. Customer must have a certified public key for verification.
13. Merchant can compute H(POD||CCD)
If H(POD||CCD)=PPD,then customer’s signature is OK.
14. Merchant forwards to acquirer CCA,POD,DS each separately encrypted using acquirer’s public key.
15. Acquirer’s forwards to bank.
16. Bank finds CCN and Amount.Verifies balance amount.Bank also verifies customer’s digital signature using CCD,POD and DS.If all OK acquirer is informed.
17. Acquirer OK’s transaction to merchant
18. Merchant supplies item.Gets payment from acquirer.Bank collects from customer.
Dual Signature System
EM: Public key of Merchant
EB: Public key of bank
(POA) EM is encrypted value with merchant’s public key
POA: (Purchase Order + Amount)
POD: Purchase Order Digest
CCA: (Credit card + Amount)
CCD: (Credit card + Amount)Digest
|| : Concatenation operator which strings together POD and CCD
PPD : Purchase Payment Digest
CPRK: Private Key of Customer, CPK: Public Key of customer
- Step1 : [(POA)EM , (CCA)EB , CCD ,DS] to Merchant
- Step2 : Merchant sends [(CCA)EB , DS , POD] to Acquirer
- Step3 : Acquirer sends (CCA)EB + DS +POD to Bank.
- Bank finds (CC No. + amount) using its private key sees if OK
Computes H(CCD||POD)
Decrypts DS with customer’s public key
If (DS)CPK = H(CCD || POD) Signature verified
- Step4 : OK to acquirer if credit and signature OK
- Step5 : Ok to Merchant
Merchant finds H(H(POA) || CCD)=PPD
Decrypts DS with public key of customer. If it gives PPD signature verified.
- Step6 : Sends delivery details
- Step7 : Bill to customer
Step1: Customer fills Purchase order, amount and credit card number in his PC. A software in PC strips it into two parts Purchase Order + Amount (POA), Credit Card No. + Amount(CCA)
POA is encrypted using merchant’s public key and CCA with bank’s public key.These are sent with customer’s public key certificates, CCD and DS.
Merchant verifies DS.
Step2: Merchant forwards to acquirer DS and CCD (These are encrypted using acquirer’s public key)
Step3: Acquirer forwards to bank. Bank decrypts CCA with its private key.Checks validity of credit card and balance. If OK informs acquirer
Step4: Acquirer OK’s transaction to merchant and credits merchant's account.
Step5: Merchant accepts customer’s order and proceeds to dispatch items. Step6: At the end of the month bank sends bill to customer.
(All these done by clicks of mouse button)
Electronic Cheque Payment
Most cheque based transactions will be between businesses -thus a special hardware is attached to PC’s for signing payments. Signature is encrypted by hardware. All public keys of business partners authenticated by certifying agencies.
Steps in transaction
1. Purchaser sends purchase order and payment advice signed with his private key to vendor.He also sends his public key certificate encrypted with vendor's public key to vendor
2. Vendor decrypts with his private key, checks certificate and cheque, attaches deposit slip, encrypts with bank's public key and sends it to bank. he also sends his public key certificate
3. Bank checks signatures, credits and clears cheque. Credit advice goes to vendor, and consolidated debit advice sent to purchaser periodically
Clearing Cheque Payment Electronically
Payments Of Small Amounts On Internet
NETBILL'S PROPRIETARY SYSTEM
•Customer charged only when information delivered
•Vendor guaranteed payment when information delivered
•Netbill is the intermediary
MAJOR STEPS
•When customer accepts quote for information, vendor sends encrypted information without key to customer
•Payment order sent to vendor with checksum of information obtained. It is
signed by customer
•Vendor sends to NET BILL copy of purchase order and the key for decryption
•NET BILL checks credit of customer. If ok it sends key to customer. Credits vendor account and debits customer account. Key sent to customer to decrypt information
•Customer decrypts information
Paying for Small Internet Transactions
Electronic Cash
•Cash for small payments
•Cash preserves anonymity
•Cash should not be traceable
•Cheaper than credit card transaction
•DES normally used for these transaction as it is cheap and amount involved is small
Traceable cash payments STEPS
1. Customer withdraws coins in various denominations signed by bank STRUCTURE------> serial no, denomination, signature of bank
Bank stores issued coins copy
2. Customer pays vendor using signed coins
3.Bank checks whether it is current or spent
4. If current it authorises dispatch of goods and credits vendor account with electronic coins
REFERENCES
1. Most of the material in this chapter are taken from Chapter 16, Electronic Commerce of the book Analysis and Design of Information Systems (2nd edition) by V.Rajaraman, Prentice-Hall of India, New Delhi,2004
2. There are many books on E-Commerce, which describe E-Commerce in detail.
Among these are:
E.Awad, Electronic Commerce, Prentice-Hall of India, New Delhi 2002.This book takes managers perspective and not very strong on technology aspects of E-Commerce. All the examples have a strong American bias as the book is primarily intended for students in America. The language is clear but the book is verbose.
What can be said in 100 pages is said in 400 pages as it includes all kinds of gossip not relevant to students wanting the learn the subject.
3. D.Minoli and E.Minoli, Web Commerce Technology Handbook, Tata McGraw-Hill, New Delhi, 1999.This book is strong in technology and has wide coverage.
4. W. Stallings, Network Security Essentials, Pearson Education Asia, New Delhi,2001. Has good presentation on DES, Triple DES, RSA and SET protocol.
5. Most traditional Systems Analysis and Design book such as the one by Kendall and Kendall do not separately discuss E-Commerce, they have a cursory treatment at various places in the book.





Comments
Post a Comment